
The Cybersecurity and Infrastructure Safety Company (CISA) warned federal businesses to patch a Zimbra Collaboration (ZCS) cross-site scripting flaw exploited by way of Russian hackers to scouse borrow emails in assaults focused on NATO international locations.
The vulnerability (CVE-2022-27926) used to be abused by way of a Russian hacking staff tracked as Iciness Vivern and TA473 in assaults on more than one NATO-aligned governments‘ webmail portals to get entry to the e-mail mailboxes of officers, governments, army team of workers, and diplomats.
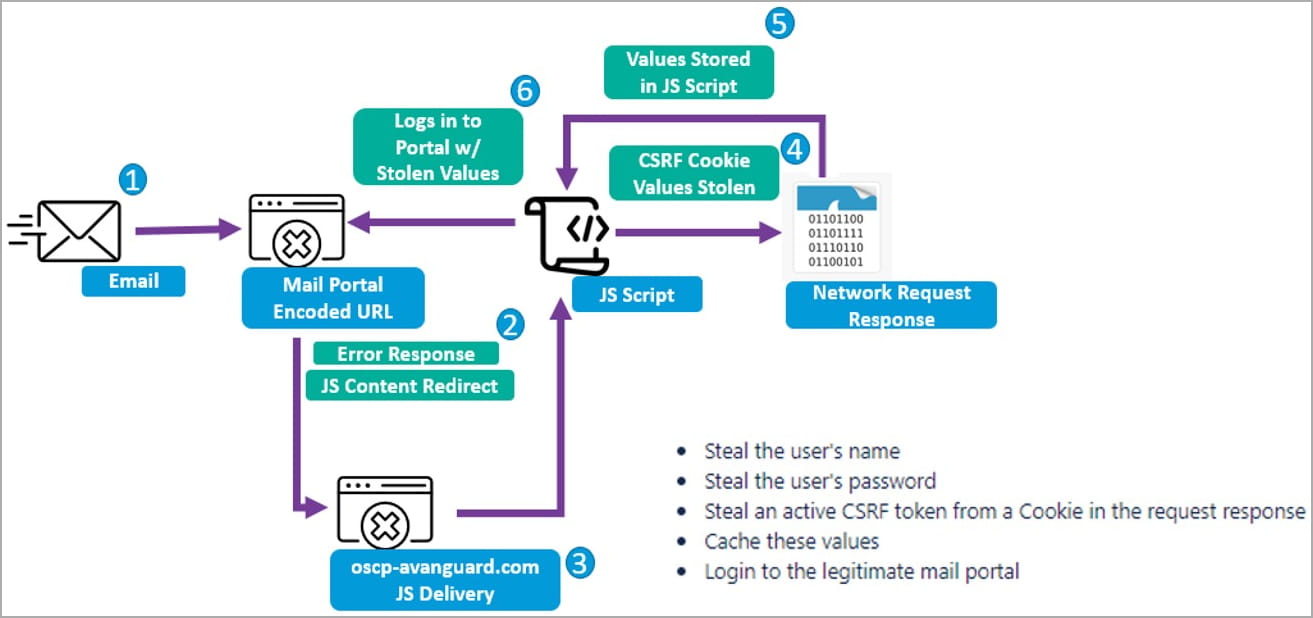
Iciness Vivern’s assaults get started with the hackers the use of the Acunetix device vulnerability scanner to seek out susceptible ZCS servers and sending customers phishing emails that spoof senders the recipients are acquainted with.
Every e-mail redirected the objectives to attacker-controlled servers that exploit the CVE-2022-27926 worm or try to trick the recipients into turning in their credentials.
When centered with an exploit, the URLs additionally include a JavaScript snippet that may obtain a second-stage payload to release a Go-Website online Request Forgery (CSRF) assault to scouse borrow Zimbra customers’ credentials and CSRF tokens.
Within the following steps, the risk actors used the stolen credentials to acquire delicate data from the breached webmail accounts or handle patience to stay monitor of exchanged emails over the years.Â
The hackers might also leverage the compromised accounts to release extra phishing assaults and increase their infiltration of centered organizations.
Federal businesses ordered to patch till April 24
The vulnerability used to be added these days to CISA’s Identified Exploited Vulnerabilities (KEV) catalog, an inventory of safety flaws recognized to be actively exploited within the wild.
In keeping with a binding operational directive (BOD 22-01) issued by way of the U.S. cybersecurity company in November 2021, Federal Civilian Govt Department Businesses (FCEB) businesses should patch susceptible methods on their networks towards insects added to the KEV listing.
CISA gave FCEB businesses 3 weeks, till April 24, to protected their networks towards assaults that will goal the CVE-2022-27926 flaw.
Whilst BOD 22-01 best applies to FCEB businesses, CISA additionally strongly recommended all organizations to prioritize addressing those insects to dam additional exploitation makes an attempt.
“These kinds of vulnerabilities are common assault vectors for malicious cyber actors and pose vital dangers to the federal undertaking,” CISA warned these days.
On Thursday, CISA additionally ordered federal businesses to patch safety vulnerabilities exploited as zero-days in contemporary assaults to deploy business spyware and adware on Android and iOS cellular units, as Google’s Danger Research Workforce (TAG) lately printed.