Quite a lot of fashionable community threats contain information robbery by means of abuse of community services and products, which is termed information exfiltration. To trace such threats, analysts track information transfers out of the groupâs community, in particular information transfers going on by means of community services and products no longer basically meant for bulk switch services and products. One such provider is the Area Title Device (DNS), which is very important for plenty of different Web services and products. Sadly, attackers can manipulate DNS to exfiltrate information in a covert approach.
This SEI weblog publish makes a speciality of how the DNS protocol will also be abused to exfiltrate information by means of including bytes of knowledge onto DNS queries or making repeated queries that include information encoded into the fields of the question. The publish additionally examines the overall visitors analytic we will use to spot this abuse and applies a number of equipment to be had to put in force the analytic. The combination dimension of DNS packets may give a in a position indicator of DNS abuse. Alternatively, for the reason that DNS protocol has grown from a easy cope with solution mechanism to dispensed database give a boost to for community connectivity, deciphering the combination dimension calls for figuring out of the context of queries and responses. By means of figuring out the amount of DNS visitors, each in isolation and in combination, analysts would possibly higher fit outgoing queries and incoming responses.
The knowledge used on this weblog publish is the CIC-BELL-DNS-EXF 2021 information set, as printed together with the paper Light-weight Hybrid Detection of Information Exfiltration the use of DNS in keeping with Device Finding out by means of Samaneh Mahdavifar et al.
The Position of DNS
DNS helps a couple of forms of queries. Those queries are described in quite a few Web Engineering Process Power (IETF) Request for Remark (RFC) paperwork. Those RFCs come with the next:
- A and AAAA queries for IP cope with similar to a website title (e.g., âwhich cope with corresponds to www.instance.com?â with a reaction like â192.0.2.27â)
- pointer report (PTR) queries for title similar to an IP cope with (e.g., âwhich title corresponds to 192.0.2.27?â with a reaction of âwww.instance.comâ)
- title server (NS), mail trade (MX), and provider locator (SRV) queries for the id of key servers in a given area
- get started of authority (SOA) queries for details about addresses on which the queried server would possibly discuss authoritatively
- certificates (CERT) queries for encryption certificate touching on the serverâs coated domain names
- textual content report (TXT) queries for additional info (as configured by means of the community administrator) in a textual content structure
A given DNS question packet will request knowledge on a given area from a selected server, however the reaction from that server would possibly come with a couple of useful resource data. The scale of the reaction depends on what number of useful resource data are returned and the kind of every report.
As soon as analysts perceive the explanations for monitoring DNS visitors and the context wanted for deciphering the monitoring effects, they are able to then decide what knowledge is desired from the monitoring. This weblog publish assumes the analyst needs to trace exterior hosts that can be receiving exfiltrated knowledge.
Review of the Analytic for Figuring out Information Exfiltration
The analytic coated on this weblog publish assumes that the networks of passion are coated by means of visitors sensors that produce community glide data or no less than packet captures that may be aggregated into community glide data. There are a selection of equipment to be had to generate those glide data. As soon as produced, the glide data are archived in a glide repository or suitable database tables, relying at the research software suite.
The method taken on this analytic is, first, to combination DNS visitors related to exterior locations appearing like servers and, 2d, to profile the visitors for those locations. Step one (affiliation) comes to figuring out DNS visitors (both by means of provider port or by means of precise exam of the applying protocol), then figuring out the exterior locations concerned. The second one step (profiling) examines what number of assets are speaking with every of the locations, the combination byte rely, packet rely, and different revealing knowledge as described within the following sections.
A number of other equipment can be utilized for this research. This weblog publish will speak about two units of SEI-developed equipment:
- The Device for Web-Degree Wisdom (SiLK) is a number of visitors research equipment evolved to facilitate safety research of enormous networks. The SiLK software suite helps the environment friendly assortment, garage, and research of community glide information, enabling community safety analysts to unexpectedly question massive ancient visitors information units. SiLK is preferably fitted to examining visitors at the spine or border of a big, dispensed endeavor or mid-sized ISP.
- Mothra is a number of Apache Spark libraries that give a boost to research of community glide data in Web Protocol Glide Data Export(IPFIX) structure with deep packet inspection fields.
Each and every of the next sections will provide an analytic for detecting exfiltration by means of DNS queries within the corresponding software set.
Enforcing the Analytic by means of SiLK
Determine 1 beneath items a sequence of SiLK instructions to put in force an analytic to hit upon exfiltration. The primary command applies a filter out to standard, benign DNS visitors, setting apart DNS visitors (recognized by means of protocol popularity as indicated by means of the applying label of 53) coming from the inner community (classless inter-domain routing [CIDR] block 192.168.0.0/16) and of reasonably lengthy (70 bytes or extra) packets. The output of the filter out is then summarized by means of vacation spot cope with and shipping protocol, counting bytes, glide data, and packets for every aggregate of cope with and protocol. The ensuing counts are handiest proven if the accrued bytes are 500 or extra. After making use of the analytic to benign DNS information, it’s implemented in the second one series to DNS information encompassing compressed information for exfiltration.
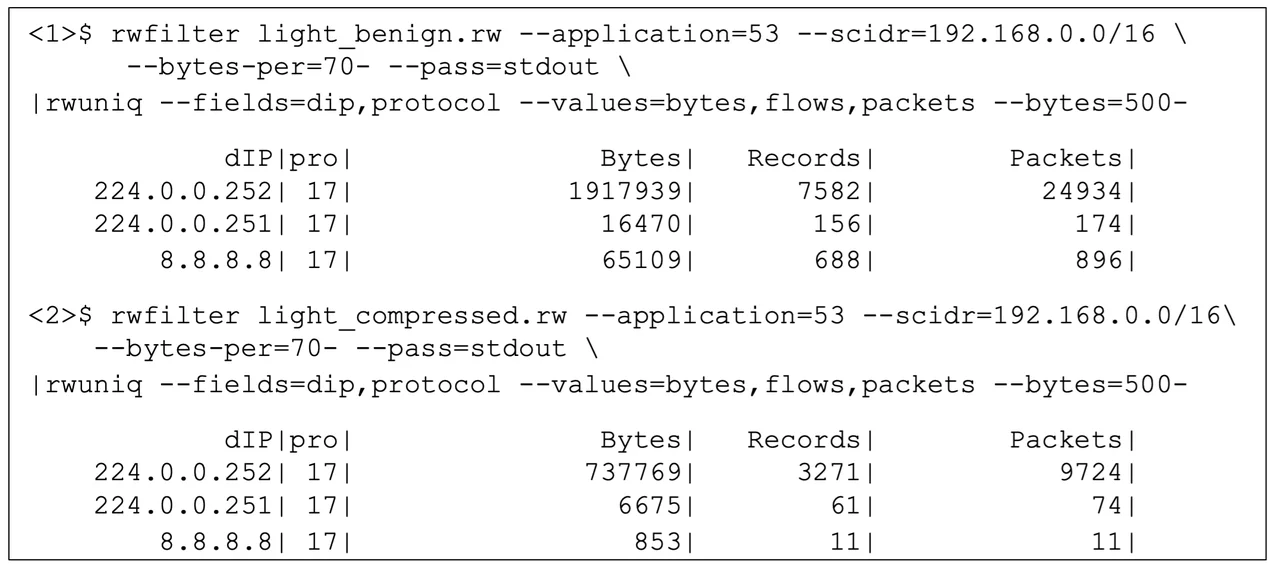
Determine 1: SiLK Analytic and Effects
The leads to Determine 1 display that the community talks to a number one DNS server, a secondary DNS server, and a public server. Within the benign case, the information is principally directed to the main DNS server and the general public server. Within the exfiltration case, the information is principally directed to the main DNS server and the secondary DNS server. This shift of vacation spot, in isolation, isn’t sufficient to make the exfiltration visitors suspicious or supply a foundation for transferring past suspicion into investigation. Within the benign case, there’s a notable fraction of the visitors directed to the general public DNS server at 8.8.8.8. Within the visitors categorised as abusive, this fraction is lessened, and the fraction to a non-public DNS server (the exfiltration goal) at 224.0.0.252 is higher. Sadly, given the restricted nature of SiLK glide data, safety analysts have a troublesome time exfiltrating further visitors. To move additional, extra DNS-specific fields are required. Those fields are equipped by means of deep packet inspection (DPI) information in expanded glide data in IPFIX structure. Whilst SiLK can not procedure IPFIX glide data, different equipment akin to Mothra and databases can.
Enforcing the Analytic by means of Mothra
Determine 2 beneath displays the analytic applied in Spark the use of the Mothra libraries. Those libraries permit definition and loading of knowledge frames with community glide report information in both SiLK or IPFIX structure. A knowledge body is a number of information arranged into named columns. Information frames will also be manipulated by means of Spark purposes to isolate flows of passion and to summarize the ones flows. Defining the information frames comes to figuring out the columns and the information to populate the columns. In Determine 2, the information frames are outlined by means of the spark.learn.box serve as and populated by means of information from both the captured benign visitors or the captured exfiltration visitors by means of Mothraâs ipfix serve as. In combination, those purposes identify the information information body.
The end result information body is made from the information information body by means of a sequence of filtering and summarization purposes. The preliminary filter out restricts it to visitors categorised as DNS visitors, adopted by means of any other filter out that guarantees the data include DNS useful resource report queries or responses. The choose serve as that follows isolates particular report options for summarization: time, visitors supply and vacation spot, byte and packet volumes, DNS names, DNS flags, and DNS useful resource report varieties. The groupBy serve as generates the summarization for every distinctive DNS title and useful resource report kind aggregate. The agg serve as specifies that the summarization include the rely of glide data, the counts of supply and vacation spot IP addresses, and the totals for bytes and packets. The filter out serve as (after the summarization) restricts output to simply the ones appearing a bytes-per-packet ratio of greater than 70 with fewer than 3 entries within the DNS Title checklist. This final filter out excludes summarizations of visitors this is massive handiest because of the duration of the reaction checklist quite than to the duration of particular person queries.
This filtering and summarization procedure creates a profile of enormous DNS requests and responses (separated by means of DNS flag values). Using DNS names as a grouping price permits the analytic to tell apart repeated queries to identical domain names. The counts of supply and vacation spot IP addresses permit the analyst to tell apart repeated visitors to a couple of places as an alternative of uncommon visitors to a couple of places or from a couple of assets.
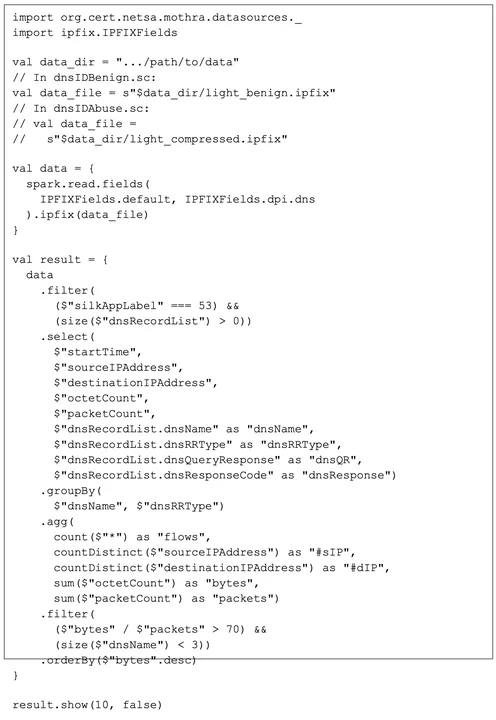
Determine 2: Mothra Implementation of Analytic
Determine 3 beneath displays the output of dnsIDExfil.sc on benign and on compressed information, the information units used within the previous SiLK dialogue. The presence of multicast (224/8 and 239/8 CIDR blocks) and RFC1918 non-public addresses (192.168/16 CIDR blocks) is because of this information coming from a man-made assortment surroundings as an alternative of are living Web visitors seize.
Contrasting the benign output proven in Determine 3 in opposition to the abuse output, we see a smaller collection of search for addresses being queried within the abuse effects and a miles faster drop-off within the collection of queries in line with host. Within the benign effects, there are six DNSNames which might be queried again and again; within the abuse effects, there are two. The entire queries proven are PTR (opposite. RRType=12) queries, and all are going to the similar server. Within the high-volume DNSName queries, the utmost reasonable packet duration is reasonably better for the abuse information than for the benign information (81 vs. 78). Taken in combination, those variations display a slow-and-steady liberate of extra information as a part of the DNS information switch, which displays the report switch happening.
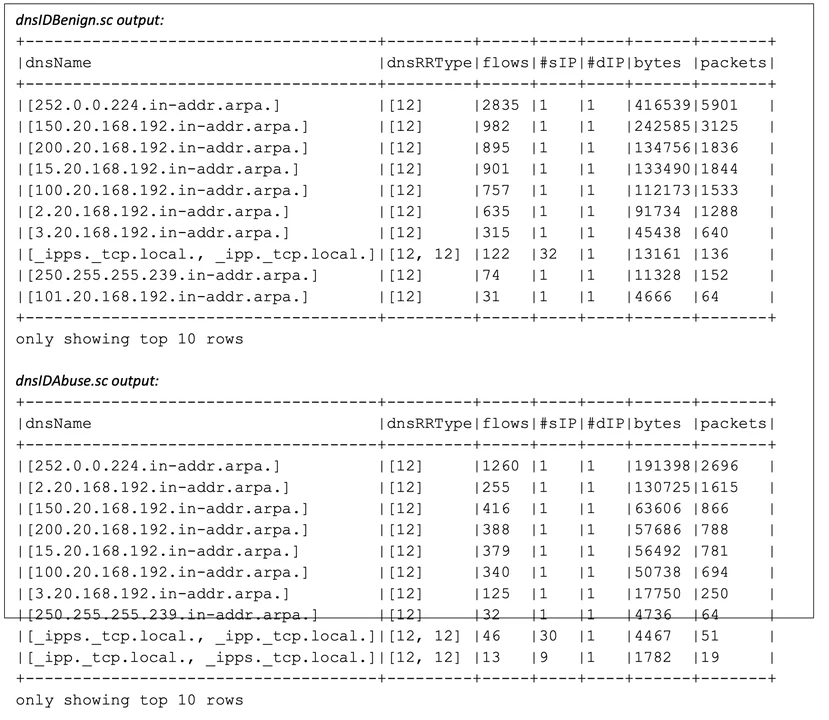
Determine 3: Output of Mothra Analytic on Benign and Exfiltration Site visitors
Figuring out Information Exfiltration
Whichever type of tooling is used, analysts incessantly want an figuring out of the information transfers from their community. Repetitive queries for DNS solution will have to be quite uncommonâcaching will have to do away with many of those repetitions. As repetitive queries for solution are recognized, a number of teams of hosts could also be discovered:
- Hosts that generate repetitive queries no longer indicative of exfiltration of knowledge are more likely to exist, characterised by means of very constant question dimension, periodic timing, and the usage of anticipated title servers.
- Hosts that generate repetitive queries with odd title servers or timing would possibly require additional investigation.
- Hosts that generate repetitive queries with odd title servers or question sizes will have to be tested moderately to spot attainable exfiltration.
The have an effect on of those hosts on community safety will range relying at the vary and criticality of belongings the ones hosts get right of entry to, however probably the most visitors would possibly call for instant reaction.
What Would possibly a Safety Analyst Wish to Know
This publish is a part of a sequence addressing a easy query: What would possibly a safety analyst need to know at the beginning of every shift in regards to the community? In every publish we will be able to speak about one resolution to this query and alertness of quite a few equipment that can put in force that resolution. Our purpose is to supply some key observations that assist analysts track and protect their networks, that specialize in helpful ongoing measures, quite than the ones particular to at least one match, incident, or factor.
We can no longer focal point on signature-based detection, since there are a number of assets for such together with intrusion detection programs (IDS)/intrusion prevention programs (IPS) and antivirus merchandise. The equipment utilized in those articles will basically be a part of the CERT/NetSA Research Suite, however we will be able to come with different equipment if useful. Previous posts tested equipment for monitoring tool updates and proxy bypass.
Our method will likely be to focus on a given analytic, speak about the inducement in the back of the analytic, and give you the utility as a labored instance. The labored instance, by means of goal, is illustrative quite than exhaustive. The verdict of what analytics to deploy, and the way, is left to the reader.
If there are certain behaviors that you just wish to recommend, please ship them by means of e mail to [email protected] with âSOC Analytics Thoughtâ within the matter line.