
A brand new ransomware gang named ‘Cash Message’ has seemed, focused on sufferers international and critical million-dollar ransoms to not leak knowledge and liberate a decryptor.
The brand new ransomware was once first reported by way of a sufferer at the BleepingComputer boards on March 28, 2023, with Zscaler’s ThreatLabz quickly after sharing data on Twitter.
Lately, the danger actor lists two sufferers on its extortion website online, one among which is an Asian airline with annual income just about $1 billion. Moreover, the danger actors declare to have stolen recordsdata from the corporate and come with a screenshot of the accessed record device as evidence of the breach.
.jpg)
Whilst investigating, BleepingComputer has observed proof of a possible Cash Message breach on a well known pc {hardware} supplier. Then again, we have now no longer been in a position to independently ascertain the assault with the corporate right now.
How Cash Message encrypts a pc
The Cash Message encryptor is written in C++ and comprises an embedded JSON configuration record figuring out how a tool can be encrypted.
This configuration record comprises what folders to dam from encrypting, what extension to append, what products and services and processes to terminate, whether or not logging is enabled, and area login names and passwords most probably used to encrypt different gadgets.
Within the pattern analyzed by way of BleepingComputer, the ransomware won’t encrypt recordsdata within the following folders:
C:msocache,C:$home windows.~ws,C:device quantity data,C:perflogs,C:programdata,C:program recordsdata (x86), C:program recordsdata,C:$home windows.~bt,C:home windows,C:home windows.outdated,C:boot]When introduced, it’ll delete Shadow Quantity Copies the use of the next command:
cmd.com /c vssadmin.exe delete shadows /all /quiet to transparent shadow quantity copiesThe ransomware will then terminate the next procedure:
sql.exe,oracle.exe,ocssd.exe,dbsnmp.exe,synctime.exe,agntsvc.exe,isqlplussvc.exe,xfssvccon.exe,mydesktopservice.exe,ocautoupds.exe,encsvc.exe,firefox.exe,tbirdconfig.exe,mdesktopqos.exe,ocomm.exe,dbeng50.exe,sqbcoreservice.exe,excel.exe,infopath.exe,msaccess.exe,mspub.exe,onenote.exe,outlook.exe,powerpnt.exe,steam.exe,thebat.exe,thunderbird.exe,visio.exe,winword.exe,wordpad.exe,vmms.exe,vmwp.exeSubsequent, the ransomware shuts down the next Home windows products and services:
vss, sql, svc$, memtas, mepocs, sophos, veeam, backup, vmmsWhen encrypting recordsdata, it’ll no longer append any extension, however this may trade relying at the sufferer. In line with safety researcher rivitna, the encryptor makes use of ChaCha20/ECDH encryption when encrypting recordsdata.
The one recordsdata excluded from encryption by way of default are:
- desktop.ini
- ntuser.dat
- thumbs.db
- iconcache.db
- ntuser.ini
- ntldr
- bootfont.bin
- ntuser.dat.log
- bootsect.bak
- boot.ini
- autorun.inf
All the way through our assessments, the encryption of the recordsdata by way of Cash Message was once moderately gradual in comparison to different encryptors.
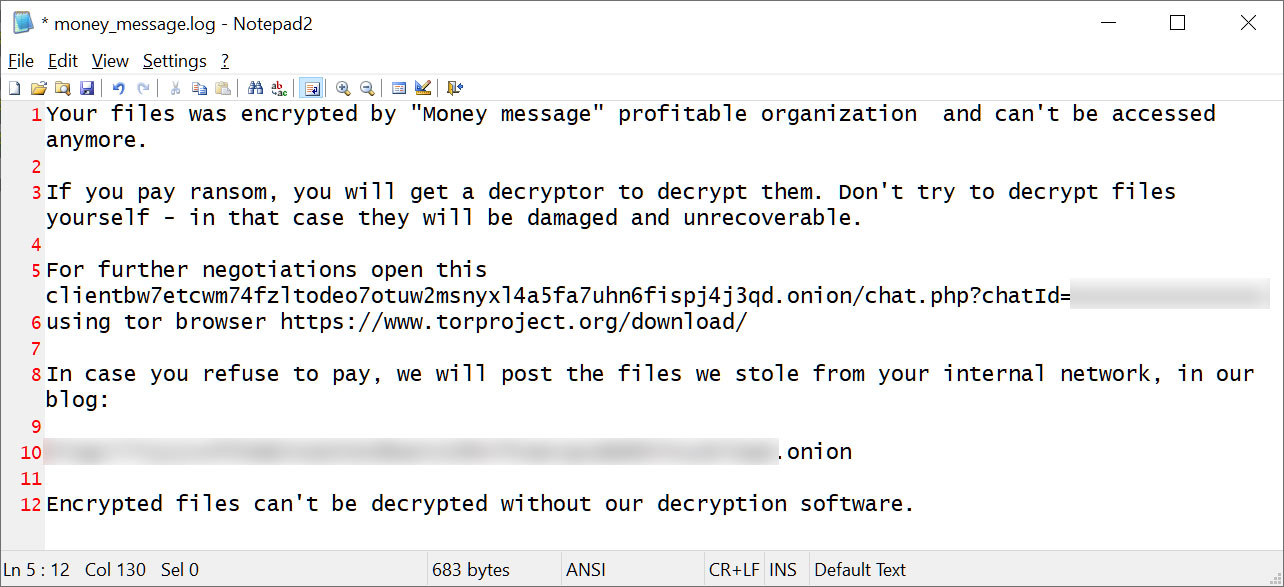
After encrypting the instrument, the ransomware will create a ransom word named money_message.log that comprises a hyperlink to a TOR negotiation website online used to barter with the danger actors.
The ransomware may also warn that they’re going to submit any stolen knowledge on their knowledge leak website online if a ransom isn’t paid.
The emergence of the Cash Message ransomware staff introduces an extra danger that organizations want to be careful for.
Even though the encryptor utilized by the crowd does no longer seem refined, it’s been showed that the operation is effectively stealing knowledge and encrypting gadgets throughout their assaults.
Professionals will analyze the ransomware, and if a weak point within the encryption is located, we can replace this put up.