Application Programs Interfaces (APIs) have actually ended up being the foundation of modern-day software application advancement in today’s connected digital environment. They permit the smooth interchange of information and performance in between systems, promoting development and enhancing user experiences. Amazon Web Solutions (AWS) has actually progressed as an essential platform for hosting and administering APIs, supplying a robust and scalable environment for developing and releasing APIs because the dawn of cloud computing. Nevertheless, higher connection features increased security vulnerabilities, making API security a leading concern for software application services business.
Intro to API Security
API security is essential in API advancement to construct and keep protected and reputable applications. It avoids unapproved gain access to, information breaches, and other security risks to your Application Setting User Interfaces. Since APIs regularly links in between various software application parts, securing them is vital for preventing vulnerabilities that may reveal delicate information or disrupt operations.
The Value of API Security
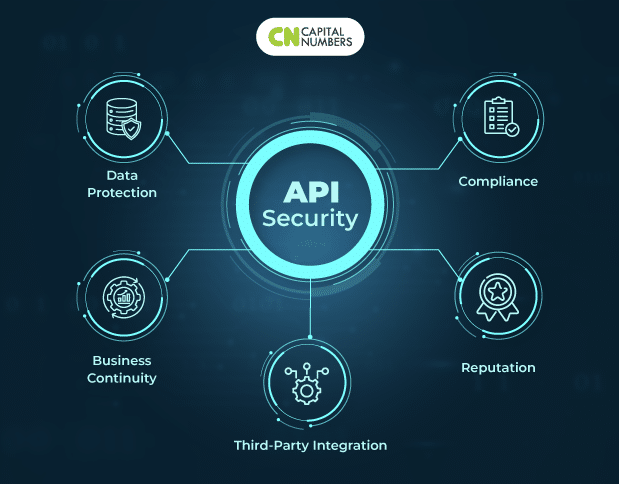
⢠Data Defense: Protecting delicate information is at the heart of the concern. APIs are utilized to interact a large range of delicate details, consisting of user passwords, individual information, monetary records, and more. In this setting, a security breach may signify catastrophe, with unimaginable effects such as information theft, identity scams, monetary losses, and irreversible reputational damage. Therefore, information security is no longer a high-end in the digital age however an essential requirement.
⢠Company Connection: Aside from information security, the stability of APIs straight effects service connection. Unsecured APIs are an open invite to hostile stars that want to interfere with systems or trigger systemic breakdowns. Such disruptions might be devastating, leading to prolonged downtimes, profits losses, and, as an outcome, a loss of self-confidence amongst clients, partners, and stakeholders.
⢠Compliance: Adherence to regulative compliance is needed in an age of increasing focus on information personal privacy and security. The General Data Defense Policy (GDPR) and the Medical Insurance Mobility and Responsibility Act (HIPAA) are 2 examples of stringent laws that a number of organizations and geographical areas have actually enacted. These requirements need strict information security practices and levy extreme fines for noncompliance. As an outcome, inadequate API security endangers information and exposes companies to considerable legal and monetary ramifications.
⢠Track Record: API security is important for brand name image upkeep in the digital environment, where track record and trust are important possessions. A security breach might irreversibly hurt a brand name’s track record and damage client self-confidence. Restoring broken trust is in some cases a massive job with long-lasting implications.
⢠Third-Party Combination: APIs are hardly ever utilized in seclusion. They routinely user interface with systems and services offered by 3rd parties. The security of your APIs straight affects the security posture of these connected systems. An unsecured API can trigger a domino effect, leading to vulnerabilities and possible breaches throughout a connected network of digital procedures.
API Security Finest Practices
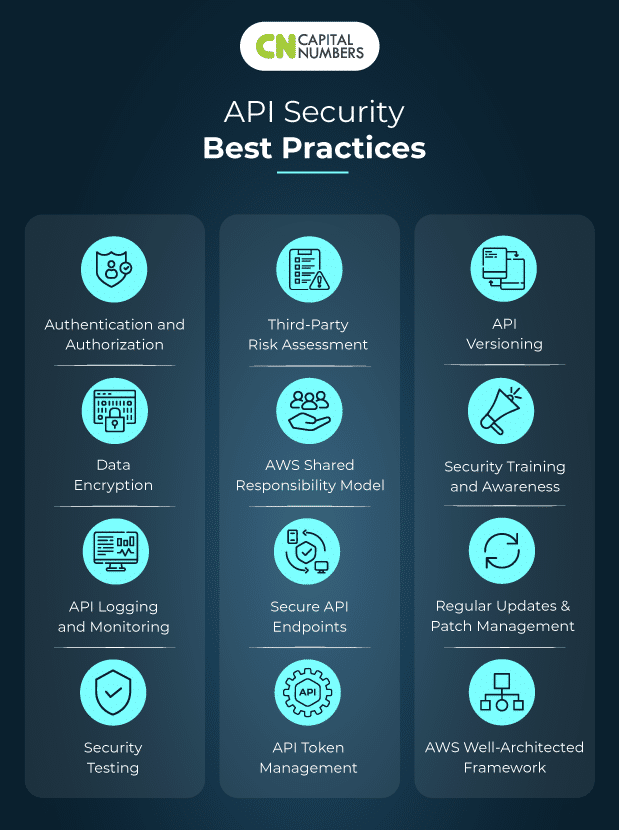
AWS professionals concentrate on API security to avoid information breaches, guarantee compliance, protect AWS resources versus unapproved gain access to, and more. Following are the complete API security finest practices advised by Capital Numbers, with a focus on AWS:
1. Authentication and Permission
- Authentication confirms the identity of users or systems attempting to access the API, while permission identifies the level of gain access to approved to validated entities.
- Utilize industry-standard authentication approaches like OAuth2, JWT (JSON Web Tokens), or API secrets.
- Take Advantage Of AWS Identity and Gain Access To Management (IAM) to handle access to AWS resources firmly. Make sure that IAM policies are distinct and restricted to the minimum needed consents.
- Appoint particular functions and consents to users or systems to guarantee they can just gain access to licensed resources.
2. Protect API Endpoints
- API endpoints are the entry indicate your system. Protecting them is an essential action in API security.
- Validate and sterilize user input to avoid typical vulnerabilities like SQL injection and Cross-Site Scripting (XSS).
- Amazon API Entrance is a vital element for handling and protecting APIs. Configure it to deal with authentication, demand recognition, and rate restricting.
- Use AWS API Entrance’s demand recognition includes to specify and implement input recognition guidelines, guaranteeing that just well-formed, safe demands reach your backend.
- Implement rate restricting utilizing AWS API Entrance’s integrated functions to avoid abuse and brute-force attacks.
3. Data File Encryption
- Securing information in transit and at rest safeguards delicate details from interception or theft.
- Usage HTTPS to secure information in transit and guarantee that your SSL/TLS certificates are updated.
- Usage AWS Certificate Supervisor (ACM) to handle SSL/TLS certificates for your AWS APIs.
- Utilize file encryption systems to safeguard information at rest or saved in databases or on disk. Make use of AWS services like Amazon S3, Amazon RDS, or AWS Secret Management Service (KMS) to secure information at rest.
- Usage AWS Secret Management Service (KMS) to handle file encryption secrets and specify fine-grained gain access to controls for information file encryption.
4. API Token Management
- Handling API tokens, such as API secrets or gain access to tokens, is vital to avoiding unapproved gain access to.
- Frequently turn API tokens to restrict direct exposure in case of compromise. Take Advantage Of Amazon API Entrance API secrets for authentication and limit gain access to based upon API secrets.
- Usage AWS API Entrance API secrets to manage access to your APIs and established use strategies to handle rate limitations and quotas.
5. API Logging and Tracking
- Extensive logging and real-time tracking assistance identify and react to security events.
- Maintain in-depth logs of API activities to track suspicious habits. Enable AWS CloudTrail to record API calls and keep an eye on AWS resource modifications.
- Implement SIEM services to keep an eye on and evaluate API logs for abnormalities. Establish Amazon CloudWatch alarms to set off notices for suspicious activities.
- Produce CloudWatch control panels and alarms to get insights into the efficiency and security of your AWS APIs.
6. API Versioning
- Maintain backwards compatibility while developing your APIs to guarantee existing combinations stay protected.
- Usage versioning plans like Semantic Versioning (SemVer) to plainly interact modifications and guarantee smooth upgrades.
7. Security Screening
- Frequently check your APIs for vulnerabilities utilizing tools like penetration screening and security scanning.
- Conduct routine penetration tests to recognize weak points in your API security. Use AWS Inspector to evaluate the security of your AWS resources and APIs.
- Utilize fixed and vibrant analysis tools to scan code for vulnerabilities. Think about utilizing third-party vulnerability scanning tools that incorporate effortlessly with AWS.
- Take Advantage Of AWS Inspector to automate security evaluation jobs, consisting of vulnerability scanning and compliance checks.
8. Security Training and Awareness
- Inform your advancement and operations groups about API security finest practices.
- Offer training on protected coding practices and typical security dangers. Benefit from AWS training resources and accreditations to guarantee your group is skilled in AWS security.
- Establish and routinely upgrade an occurrence reaction strategy to attend to security breaches without delay. Produce a particular occurrence reaction prepare for AWS to deal with security events within the AWS Cloud.
9. Third-Party Danger Evaluation
- Evaluate the security practices of third-party APIs your system connects with.
- Examine the security controls and practices of third-party API suppliers prior to combination.
10. Routine Updates and Spot Management
- Keep your API structures, libraries, and dependences up-to-date to alleviate recognized vulnerabilities.
- Display security advisories and use spots without delay to attend to recognized vulnerabilities.
11. AWS Shared Obligation Design
- Comprehend the AWS Shared Obligation Design, which specifies the department of security duties in between AWS and the client.
- Understand your duties for protecting information and setups within AWS services.
12. AWS Well-Architected Structure
- Follow the AWS Well-Architected Structure’s security finest practices to develop and run protected and durable work.
- Pay specific attention to the Security Pillar of the AWS Well-Architected Structure, which guides on carrying out security finest practices.
Likewise Check Out: What Is Serverless Computing?
Conclusion
API security within the AWS environment is important to modern-day cloud computing. Capital Numbers, a trustworthy software application services business, acknowledges the value of securing your information in the age of interconnected systems and APIs hosted on AWS. By following these detailed API security finest practices particularly customized for the AWS environment, you can considerably lower the danger of security breaches, safeguard your information, and keep the trust of your clients and partners. Keep in mind that API security is not a one-time effort however a continuous dedication to remain ahead of developing digital and cloud computing dangers. Stay alert, notified, and proactive in protecting your APIs in the AWS cloud.